In this post I'll try to show how to reach the same functionality connecting your PC to the iphone over cable with the help of OpenVPN. Why OpenVPN? Because it is the only vpn suite which can use TCP protocol and one port for connection. That's why we can arrange ssh local tunnel to link the PC with external vpn server over iphone's GPRS/EDGE/3G.
OpenVPN is a great cross-platform freeware and open source program for creating virtual private network (VPN) between computers. I found some original guides in linux guru blogs (here and here) so my idea is only to repeat the same tricks for Windows.
We need two PCs, one is a laptop to be tethered where we'll install openvpn client. Another machine is home or small-office PC connected to broadband Internet line and to be configured as openvpn server.
The main idea of VPN is gaining secure access to the intranet shared resources, company internal web-site or mailserver over fast Internet line through encrypted tunnel between client and server hosts. In addition, vpn-server can be a kind of "router" for the remote vpn-client giving full Internet access to it. Typically it's not needed because vpn-client is already in the Internet and gains only access to the private resources at the server's LAN. But in our case it is essential, the laptop will be connected to the vpn server over GPRS/EDGE/3G and get full Internet access from it. All requests will be wrapped into openvpn tunnel which in turn will be wrapped into ssh tunnel between ssh-client, the laptop, and ssh-server, the iphone. Sounds complicated? Let's see.
First, we need to install and configure our openvpn hosts. The latest release version of openvpn is 2.09, you can download it from official page at http://www.openvpn.net/index.php/downloads.html, there is GUI interface for Windows at http://openvpn.se. Besides, the new openvpn version 2.1 (pre-release is available) supports Vista and contains GUI already inside. I experimented with this pre-release version on my Vista Home Premium laptop connecting it to my office openvpn 2.09 server without problem.
The installation is rather easy, one extra tun/tap pseudo network adapter is added to each system. This adapter will be used for point-to-point connection, it is fully controlled by openvpn so don't touch it at all.
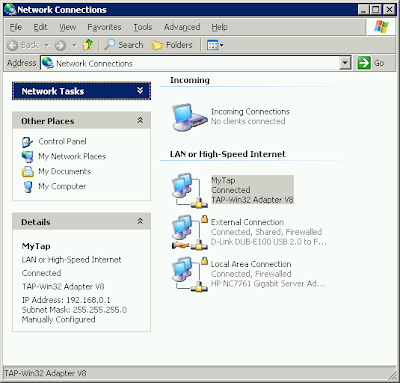
Assume we have openvpn server with fictitious address remote.vpn.com somewhere in Internet. This server has two real Ethernet adapters. One is for external connection, another is part of small-office LAN within 172.29.10.x range, this LAN adapter address is 172.29.10.10, the third "adapter" is openvpn MyTap. So server's Network Places look like this (ignore Incoming connections here):
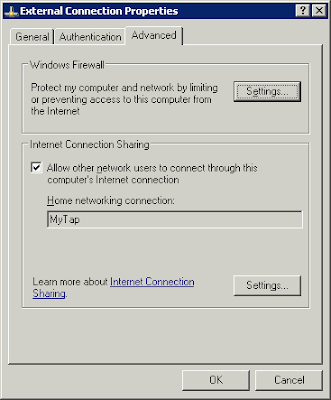
 In order to provide the Internet access for MyTap adapter, i.e. for vpn-client, we will enable Internet Connection Sharing on External Connection for MyTap adapter
In order to provide the Internet access for MyTap adapter, i.e. for vpn-client, we will enable Internet Connection Sharing on External Connection for MyTap adapter
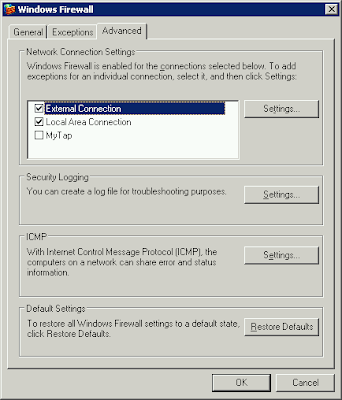
 and disable the Windows Firewall on MyTap adapter
and disable the Windows Firewall on MyTap adapter
 We need to prepare and tune up ovpn configuration file, one on laptop, another on server, samples are stored in sample-config subdirectory. So just copy client.ovpn from sample-config to config subdirectory on laptop, do the same for server.ovpn on your server. Note that openvpn is rather sensitive for config files changes so please modify them if you know what you do.
We need to prepare and tune up ovpn configuration file, one on laptop, another on server, samples are stored in sample-config subdirectory. So just copy client.ovpn from sample-config to config subdirectory on laptop, do the same for server.ovpn on your server. Note that openvpn is rather sensitive for config files changes so please modify them if you know what you do.
For both config.ovpn and client.ovpn it is essential to have:
# Are we connecting to a TCP or
# UDP server? Use the same setting as
# on the server.
proto tcp
;proto udp
and
# "dev tun" will create a routed IP tunnel,
# "dev tap" will create an ethernet tunnel.
# Use "dev tap0" if you are ethernet bridging
# and have precreated a tap0 virtual interface
# and bridged it with your ethernet interface.
# If you want to control access policies
# over the VPN, you must create firewall
# rules for the the TUN/TAP interface.
# On non-Windows systems, you can give
# an explicit unit number, such as tun0.
# On Windows, use "dev-node" for this.
# On most systems, the VPN will not function
# unless you partially or fully disable
# the firewall for the TUN/TAP interface.
dev tap
;dev tun
For client.ovpn we use 127.0.0.1 for ssh tunnel connection, not real server address here.
# The hostname/IP and port of the server.
# You can have multiple remote entries
# to load balance between the servers.
remote 127.0.0.1 1194
For server.ovpn we need to append (highlighted in blue) the following section:
# If enabled, this directive will configure
# all clients to redirect their default
# network gateway through the VPN, causing
# all IP traffic such as web browsing and
# and DNS lookups to go through the VPN
# (The OpenVPN server machine may need to NAT
# the TUN/TAP interface to the internet in
# order for this to work properly).
# CAVEAT: May break client's network config if
# client's local DHCP server packets get routed
# through the tunnel. Solution: make sure
# client's local DHCP server is reachable via
# a more specific route than the default route
# of 0.0.0.0/0.0.0.0.
push "redirect-gateway def1"
and these
# Configure server mode and supply a VPN subnet
# for OpenVPN to draw client addresses from.
# The server will take 10.8.0.1 for itself,
# the rest will be made available to clients.
# Each client will be able to reach the server
# on 10.8.0.1. Comment this line out if you are
# ethernet bridging. See the man page for more info.
;server 10.8.0.0 255.255.255.0
server 192.168.0.0 255.255.255.0
# Certain Windows-specific network settings
# can be pushed to clients, such as DNS
# or WINS server addresses. CAVEAT:
# http://openvpn.net/faq.html#dhcpcaveats
push "dhcp-option DNS 192.168.0.1"
push "dhcp-option WINS 192.168.0.1"
OpenVPN is a great cross-platform freeware and open source program for creating virtual private network (VPN) between computers. I found some original guides in linux guru blogs (here and here) so my idea is only to repeat the same tricks for Windows.
We need two PCs, one is a laptop to be tethered where we'll install openvpn client. Another machine is home or small-office PC connected to broadband Internet line and to be configured as openvpn server.
The main idea of VPN is gaining secure access to the intranet shared resources, company internal web-site or mailserver over fast Internet line through encrypted tunnel between client and server hosts. In addition, vpn-server can be a kind of "router" for the remote vpn-client giving full Internet access to it. Typically it's not needed because vpn-client is already in the Internet and gains only access to the private resources at the server's LAN. But in our case it is essential, the laptop will be connected to the vpn server over GPRS/EDGE/3G and get full Internet access from it. All requests will be wrapped into openvpn tunnel which in turn will be wrapped into ssh tunnel between ssh-client, the laptop, and ssh-server, the iphone. Sounds complicated? Let's see.
First, we need to install and configure our openvpn hosts. The latest release version of openvpn is 2.09, you can download it from official page at http://www.openvpn.net/index.php/downloads.html, there is GUI interface for Windows at http://openvpn.se. Besides, the new openvpn version 2.1 (pre-release is available) supports Vista and contains GUI already inside. I experimented with this pre-release version on my Vista Home Premium laptop connecting it to my office openvpn 2.09 server without problem.
The installation is rather easy, one extra tun/tap pseudo network adapter is added to each system. This adapter will be used for point-to-point connection, it is fully controlled by openvpn so don't touch it at all.
Assume we have openvpn server with fictitious address remote.vpn.com somewhere in Internet. This server has two real Ethernet adapters. One is for external connection, another is part of small-office LAN within 172.29.10.x range, this LAN adapter address is 172.29.10.10, the third "adapter" is openvpn MyTap. So server's Network Places look like this (ignore Incoming connections here):
 In order to provide the Internet access for MyTap adapter, i.e. for vpn-client, we will enable Internet Connection Sharing on External Connection for MyTap adapter
In order to provide the Internet access for MyTap adapter, i.e. for vpn-client, we will enable Internet Connection Sharing on External Connection for MyTap adapter and disable the Windows Firewall on MyTap adapter
and disable the Windows Firewall on MyTap adapter We need to prepare and tune up ovpn configuration file, one on laptop, another on server, samples are stored in sample-config subdirectory. So just copy client.ovpn from sample-config to config subdirectory on laptop, do the same for server.ovpn on your server. Note that openvpn is rather sensitive for config files changes so please modify them if you know what you do.
We need to prepare and tune up ovpn configuration file, one on laptop, another on server, samples are stored in sample-config subdirectory. So just copy client.ovpn from sample-config to config subdirectory on laptop, do the same for server.ovpn on your server. Note that openvpn is rather sensitive for config files changes so please modify them if you know what you do.For both config.ovpn and client.ovpn it is essential to have:
# Are we connecting to a TCP or
# UDP server? Use the same setting as
# on the server.
proto tcp
;proto udp
and
# "dev tun" will create a routed IP tunnel,
# "dev tap" will create an ethernet tunnel.
# Use "dev tap0" if you are ethernet bridging
# and have precreated a tap0 virtual interface
# and bridged it with your ethernet interface.
# If you want to control access policies
# over the VPN, you must create firewall
# rules for the the TUN/TAP interface.
# On non-Windows systems, you can give
# an explicit unit number, such as tun0.
# On Windows, use "dev-node" for this.
# On most systems, the VPN will not function
# unless you partially or fully disable
# the firewall for the TUN/TAP interface.
dev tap
;dev tun
For client.ovpn we use 127.0.0.1 for ssh tunnel connection, not real server address here.
# The hostname/IP and port of the server.
# You can have multiple remote entries
# to load balance between the servers.
remote 127.0.0.1 1194
For server.ovpn we need to append (highlighted in blue) the following section:
# If enabled, this directive will configure
# all clients to redirect their default
# network gateway through the VPN, causing
# all IP traffic such as web browsing and
# and DNS lookups to go through the VPN
# (The OpenVPN server machine may need to NAT
# the TUN/TAP interface to the internet in
# order for this to work properly).
# CAVEAT: May break client's network config if
# client's local DHCP server packets get routed
# through the tunnel. Solution: make sure
# client's local DHCP server is reachable via
# a more specific route than the default route
# of 0.0.0.0/0.0.0.0.
push "redirect-gateway def1"
and these
# Configure server mode and supply a VPN subnet
# for OpenVPN to draw client addresses from.
# The server will take 10.8.0.1 for itself,
# the rest will be made available to clients.
# Each client will be able to reach the server
# on 10.8.0.1. Comment this line out if you are
# ethernet bridging. See the man page for more info.
;server 10.8.0.0 255.255.255.0
server 192.168.0.0 255.255.255.0
# Certain Windows-specific network settings
# can be pushed to clients, such as DNS
# or WINS server addresses. CAVEAT:
# http://openvpn.net/faq.html#dhcpcaveats
push "dhcp-option DNS 192.168.0.1"
push "dhcp-option WINS 192.168.0.1"
At this point we consider openvpn configuration finished. I intentionally skip the important part of secure keys generating. It is described in details in hundreds of online openvpn manuals and guides. Remember, you must generate client keys on server console and then transfer them to client for further use.
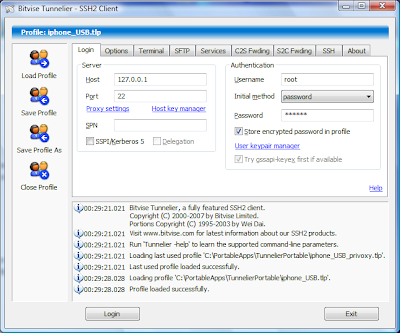
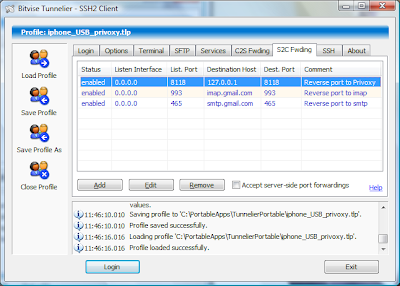
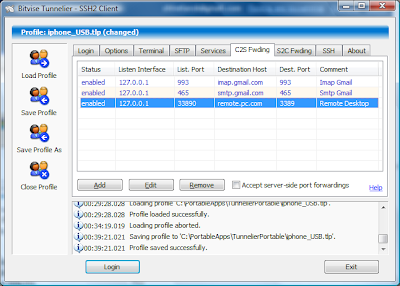
Let's return to our ssh-client on laptop and configure Tunnelier (which we so successfully used before) to arrange the only one C2S tunnel. Please disable any other options which we used before for socks-proxy and mail tunnels (see my older posts). Now we have only this entry in C2S Forwarding screen:
 where remote.vpn.com is our openvpn server address in the Internet and 1194 is port OpenVPN uses.
where remote.vpn.com is our openvpn server address in the Internet and 1194 is port OpenVPN uses.We connect the iphone to the laptop with USB cable, check ssh is ON in iphone's Bossprefs, change auto-lock to Never and start Runtunnel.cmd on laptop to enable itunnel (see my older posts). Make sure the GPRS/EDGE/3G is available on the iphone and press Login in Tunnelier.
If ssh connection is OK you can start openvpn client connection. Use OpenvpnGUI icon in tray to start openvpn session. If it's successful the laptop's tap-adapter will get 192.168.0.2 from openvpn server which according to ICS main rule keeps 192.168.0.1 for itself.
The server provides full NAT (network address translation) for client's requests wrapped into openvpn tunnel. Then the client gains FULL Internet access directly, now without any changes in its browser/mailer/im configuration. You can easily start, for instance, ftp-session or mail client or RDP in your notebook without any extra preparations. Moreover, after openvpn you can even start PPTP/L2TP/IPSec vpn connection with some third-party vpn-server which was not possible before because of ssh limitation to serve TCP protocol only.
As a result, we have encrypted and compressed openvpn tunnel between laptop and soho server on TCP port 1194 and get FULL Internet access for laptop over GPRS/EDGE/3G provided by iphone!